
Crypto custodians 2025: who safeguards institutional private keys
What are crypto custodians and why are they called “banks of custody”? We explain their role in seed phrase protection, HSM and MPC tech, and the leaders of 2025.
2025-09-24
Authorization is required only to use the service «Team energy»
Enter the e-mail you provided during registration and we will send you instructions on how to reset your password.
An error occurred while processing your request. Please try again later. If the problem persists, please contact our support team.
Seed phrase protection in 2025 is a multi-layered system: geo-decentralization, multisig, and cryptographic modules. In this article, we explore corporate practices and real cases of asset recovery.
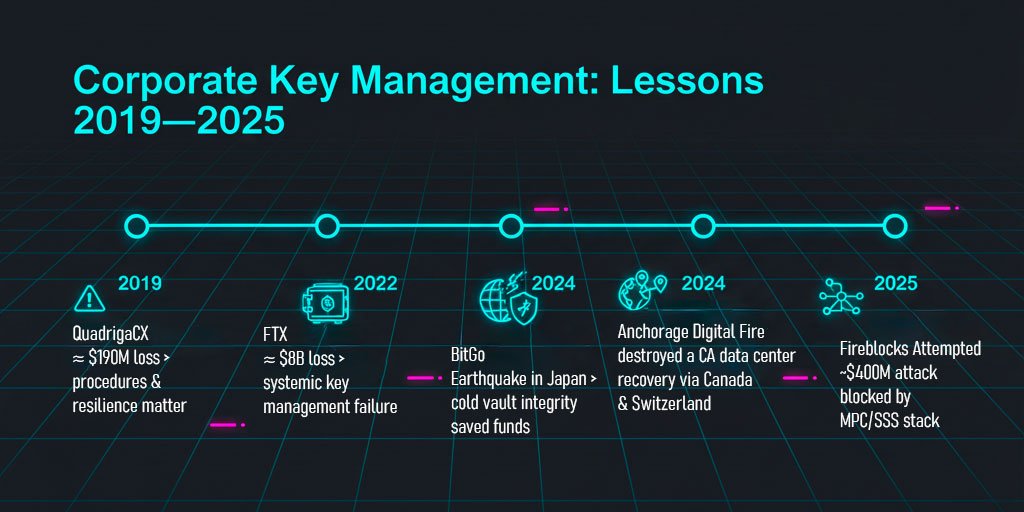
A seed phrase is the master key to your crypto. Storage mistakes have cost the industry billions: FTX lost $8B, QuadrigaCX $190M. Major players learned their lessons and built corporate-grade methods to protect seed phrases: splitting them, storing parts in different regions, using HSMs, and multisig. This article will show you the approaches custodians are using in 2025 and which of them private users can adopt to secure their assets.
In 2025, with hackers armed with AI algorithms and regulators demanding bank-level standards, institutional players like Binance or BlackRock don't rely on paper or flash drives. They build multi-layered systems, and for them, securing a seed phrase from a breach is fundamental.
Storing a seed phrase offline is the cornerstone of corporate security. Unlike retail users who jot down their seed on paper, companies use isolated media: titanium plates (CryptoSteel), encrypted USB drives, or paper in tamper-evident, sealed containers. These are kept in biometric safes or high-security bank vaults.

The process is as follows:
In 2023, Coinbase Custody saved $1 billion in assets: hackers breached online systems, but the offline keys in European vaults remained untouched. Elliptic confirms: 90% of custodial services HODL 80% of client assets in offline cold storage using seed phrases.
HSM for crypto security are cryptographic chips that never expose the seed phrase in a readable format. They generate, store, and sign keys internally, following a "never in clear" principle. A hacking attempt self-destructs the data.
This method is used by:
The infrastructure costs $0.5-2 million but pays off: HSMs meet US security standards like FIPS 140-2 and AML requirements. The downside is vendor lock-in and complex integration, which requires cryptographers.
Multisignature wallets for institutional players distribute responsibility. A transaction requires signatures from multiple parties (e.g., 5-of-7). This protects against insider threats and single-point hacks. In 2024, BitGo prevented a $100 million theft this way: one key was compromised, but the transaction failed without the others.
The setup process:
Multisig reduces potential losses by 70%. However, transaction delays and the risk of multiple key compromises demand strict audits.
The Shamir's Secret Sharing scheme (SSS) splits a seed phrase into parts, but not all fragments are needed for recovery—only a certain threshold (e.g., 3-of-5). This method is ideal for large portfolios.
The Shamir's Secret Sharing algorithm:
In 2024, Anchorage Digital saved a $2 billion fund: hackers seized one shard in Asia, but without the other two (in the US and Europe), the attack failed. CoinDesk reports: 60% of custodians use Shamir in 2025.
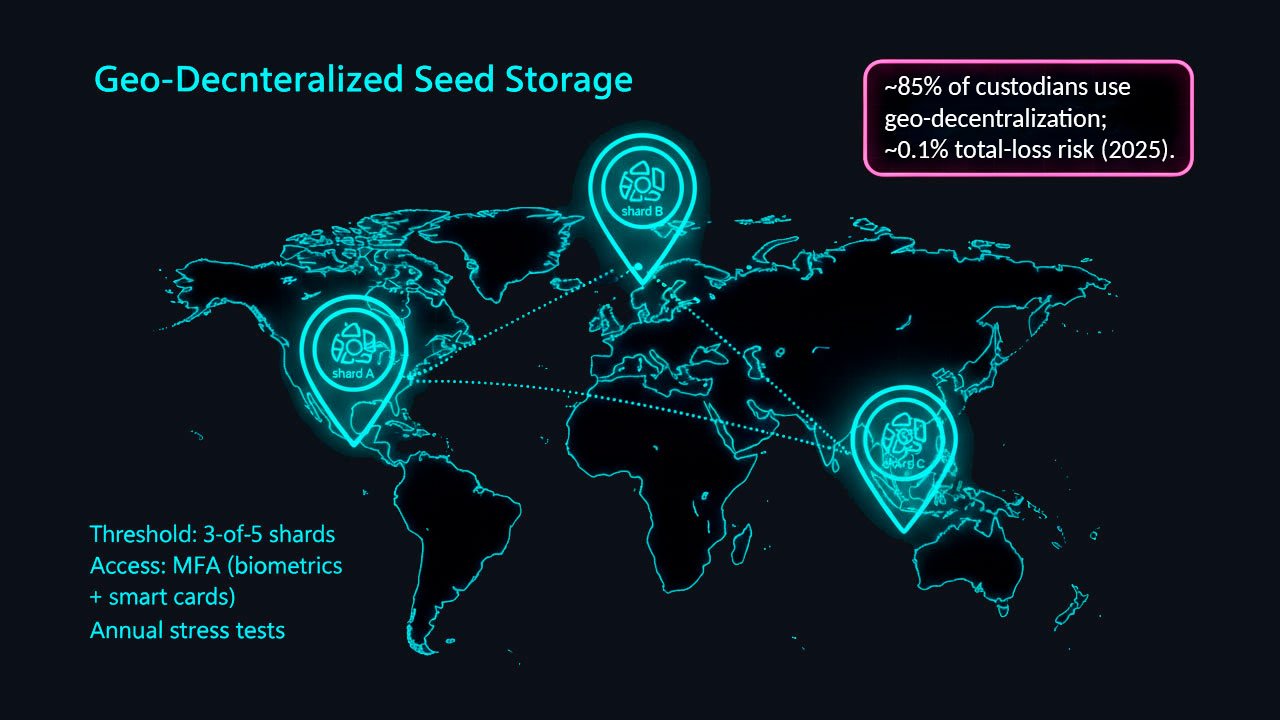
To protect against catastrophes—fires, wars, or local attacks—companies use geographic decentralization. The seed phrase or its shards are distributed across data centers and bank vaults in different countries: Switzerland, Singapore, the USA.
PwC notes that in 2025, 85% of custodians use this method, reducing the risk of total loss to 0.1%. The process looks like this:
In 2024, Anchorage Digital secured a client's $1.5 billion: a fire destroyed a data center in California, but keys in Canada and Switzerland ensured recovery. In 2025, Coinbase Custody protected an ETF by distributing keys between London, New York, and Tokyo, surviving an outage at one center.
Multi-Party Computation (MPC) is an approach where a seed phrase never exists as a whole. The key is "smeared" across servers, and transactions are signed via distributed computation. This eliminates a single point of failure.
In March 2025, Fireblocks thwarted a $400 million attack: hackers breached one server, but without the other nodes, the transaction was blocked.
Setting up Multi-Party Computation (MPC):
Gartner predicts that by 2027, 80% of custodians will switch to MPC, as it combines speed and security. The downsides are cost (millions of dollars) and provider dependency.
Custodians learn from real-world events. In 2025, Fireblocks saved a client's $500M ETF by combining shamir secret sharing crypto and mpc crypto custody: keys were split between a bank, an auditor, and data centers. An insider attack failed due to an insufficient number of signatures.
In 2024, BitGo protected $1 billion after an earthquake in Japan: their vault in Tokyo with offline seed phrase storage remained intact. These cases show that a multi-layered strategy is the key to crypto security in 2025.
| Method | Pros | Cons |
|---|---|---|
| Cold Storage | Complete isolation from hackers, durable media | Slow access, high cost of vaults |
| HSM | Keys are never exposed, quantum-resistant | Expensive, complex integration |
| Multisig | Insider protection, flexible schemes | Transaction delays, management overhead |
| Shamir's Sharing | Fault tolerance, integrates with HSMs | Complex management, human factor risk |
| Geo-Decentralization | Disaster-proof, extremely low risk of total loss | Logistics, coordination challenges |
| MPC | No single key, high transaction speed | High cost, technology is still new |
Corporate seed phrase storage methods are a must for those managing billions. FTX (8Blostin2022) and QuadrigaCX (190M in 2019) proved that without a systematic approach, collapse is inevitable.
Retail users can borrow these methods: use Shamir's Secret Sharing for fragmentation, store copies in different locations, and avoid clouds. Today, the best ways to store a seed phrase involve a synergy of technologies.
Custodians prove that crypto security in 2025 is a multi-layered fortress where each level reinforces the others. Implement at least some of their approaches, and your assets will become virtually untouchable.