
TRON Energy — Practical Use for Saving on Fees (TRON ENERGY)
What is TRON Energy and how does it help save on USDT TRC-20 transfer fees?
We explain how to use TRON ENERGY instead of burning TRX: rental, staking, and transaction packages.
2025-07-30
Authorization is required only to use the service «Team energy»
Enter the e-mail you provided during registration and we will send you instructions on how to reset your password.
An error occurred while processing your request. Please try again later. If the problem persists, please contact our support team.
Geodistribution means offline storage of keys with fragments placed in different countries. See how corporations apply this cybersecurity standard.
In 2025, basic methods for storing seed phrases are considered obsolete. Companies manage massive assets, and corporations understand that storing keys in a single location creates a critical single point of failure. That's why leading firms apply different standards: keys are not just stored offline—they are split into shards and placed in various physical and legal locations.
This method of private key storage is called "geo-distribution." Banks, funds, and exchanges are implementing multi-layered systems with regulated physical and legal protection protocols. Only a multi-step authorization system allows this operation to be executed securely.
This is the new corporate standard. In this article, we’ll explore how companies actually fragment access and bring key storage into the realm of geopolitics.
Geo-distribution of keys has become a part of corporate cybersecurity standards, alongside risk management and business continuity procedures. This isn't just a buzzword; it's a response to real technological, legal, and human threats. Companies dealing with digital assets face not only hackers but also the risk of local access restrictions, natural disasters, and internal breaches. Therefore, it's critical not only to physically isolate keys from the network but also to eliminate the risk of their loss or seizure through centralized access. Storing a seed phrase offline mitigates 95% of threats (according to Elliptic).
Online systems are targets for phishing and malware, but offline keys on isolated devices can withstand even global outages. Companies like Coinbase keep 85% of their assets in cold storage. This eliminates the risk of losing access to all assets simultaneously due to a single incident.
For firms, cryptocurrency cold storage is a multi-layered architecture. Below are the methods they employ.
Air-Gapped Key Generation and Media
In corporate crypto practice, keys are never born on a laptop running Zoom or email. They are generated on air-gapped machines, physically disconnected from any network. The result is stored on various media types: from classic paper and metal plates to encrypted hardware devices where even tampering with the casing won't reveal the seed phrase. The logic is simple: one medium is a vulnerability, while a combination of different environments provides enhanced resilience.
Multi-Factor Access: PIN/Smart Cards/Biometrics
Here, companies integrate multiple layers of authentication and authorization. A single password or PIN isn't enough; they require smart cards, tokens, and even employee biometrics. The scenario: a safe will only open if several factors match simultaneously. This approach mitigates the risk of a single insider or a data leak compromising a billion-dollar stack.
Audits, Media Rotation, and Integrity Checks
Cold storage isn't a "set it and forget it" solution. Periodic audits and access tests confirm that the keys are still in place and undamaged. Media is rotated: old copies are replaced with new ones to prevent material degradation or outdated encryption standards. Integrity checks are conducted with the same diligence as a bank vault inspection. As a result, cold storage is kept up-to-date.
This involves distributing shards across continents so that a single disaster doesn't wipe out everything.
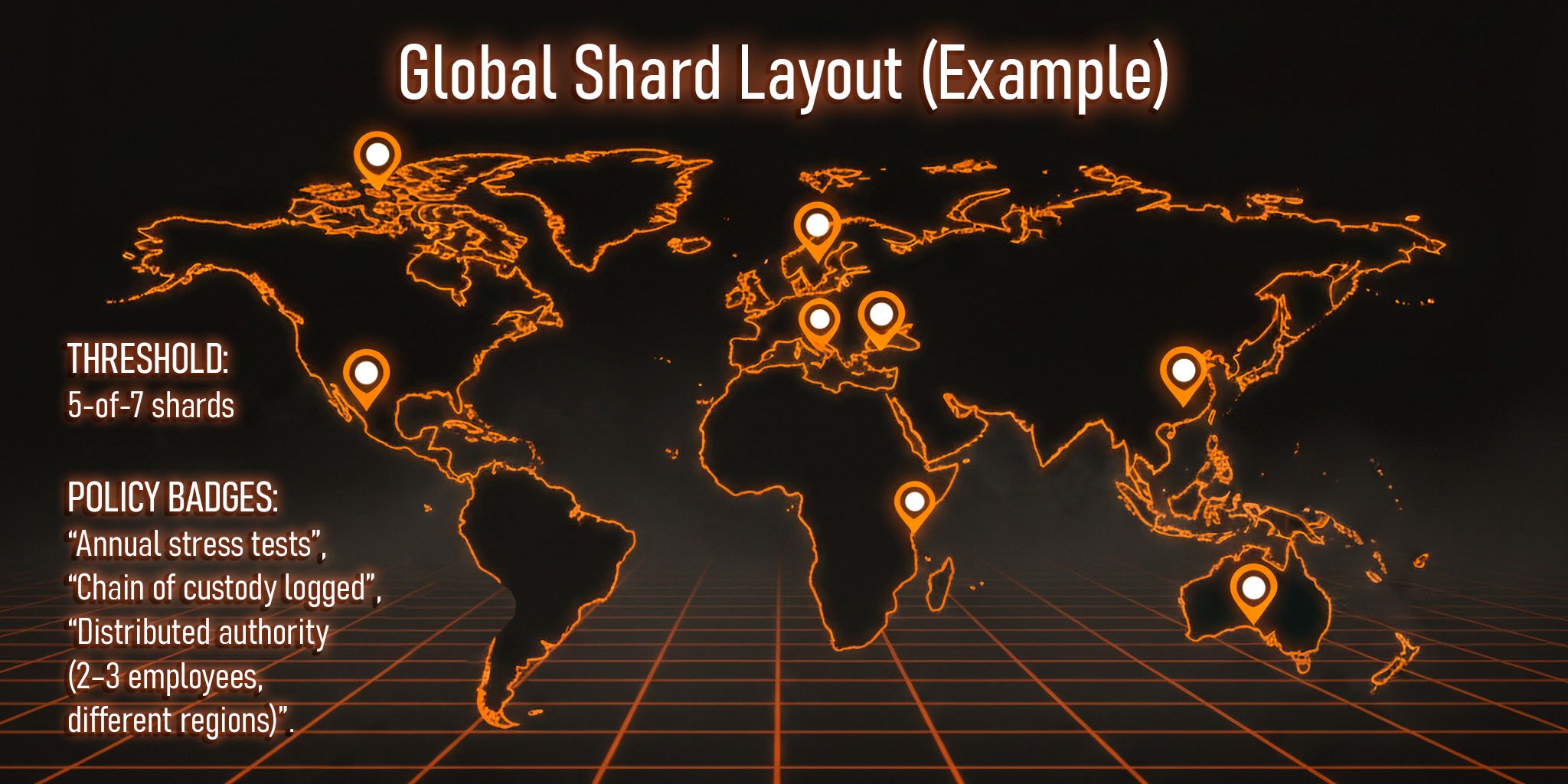
Choosing Countries and Locations
The choice of key storage locations is dictated by geopolitical and legal considerations. Companies select jurisdictions not for their fancy offices, but based on three parameters: political stability, legal framework, and physical security. Seismic activity, floods, and other cataclysms are also factored in: no one wants to store a key shard in a region prone to earthquakes every five years.
Access Policies
To eliminate the risk of single-person control, "distributed authority" schemes are introduced. Access to shards is possible only with the participation of two or three trusted employees from different regions. It’s like a multi-sig, but implemented at the level of distributed regional centers: one in London, a second in Singapore, and a third in Toronto. No single insider can pull off an operation alone.
Logistics, Chain of Custody, and Annual Stress Tests
Storing shards is a science. Companies document the entire chain of custody: who accessed the medium, when, and where. Every movement is recorded as if it were a highly regulated transfer chain with every action logged. Annual stress tests are conducted to simulate disaster scenarios—from communication blackouts to the loss of a safe—to verify if the system can recover without panic or downtime.
Insider Case Study: When Decentralization Was Only on Paper
In 2024, a top-20 exchange created a major headache for itself precisely because its "geo-distribution" was a sham. Two of the three key shard custodians flew to the same conference. On the day access was needed, the airport was hit by a staff strike: flights were delayed for three days, and people were stuck in the transit zone.

For three days, the company was unable to sign a portion of its transactions—millions of dollars were frozen. Internally, they called it a "temporary inability to execute transactions due to the unavailability of authorized personnel"—a phrase concealing an operational failure. After the incident, the policy was rewritten strictly: now, at least two custodians must be in different countries with independent logistics routes.
The irony is that, technically, the system looked flawless, but it was compromised by the human factor and basic logistics. This incident showed that even well-designed technical systems are not immune to logistical and access management oversights. Companies facing such failures are now revising protocols, including requirements for the physical location of custodians, minimum availability when planning travel, flexible activation of backup routes, and strict controls.
Shamir's Secret Sharing (SSS) and multi-signature are powerful tools on their own. But in the corporate reality of 2025, they are increasingly used in tandem to eliminate even a hint of a single point of failure.
Why combine them? These methods work as follows:
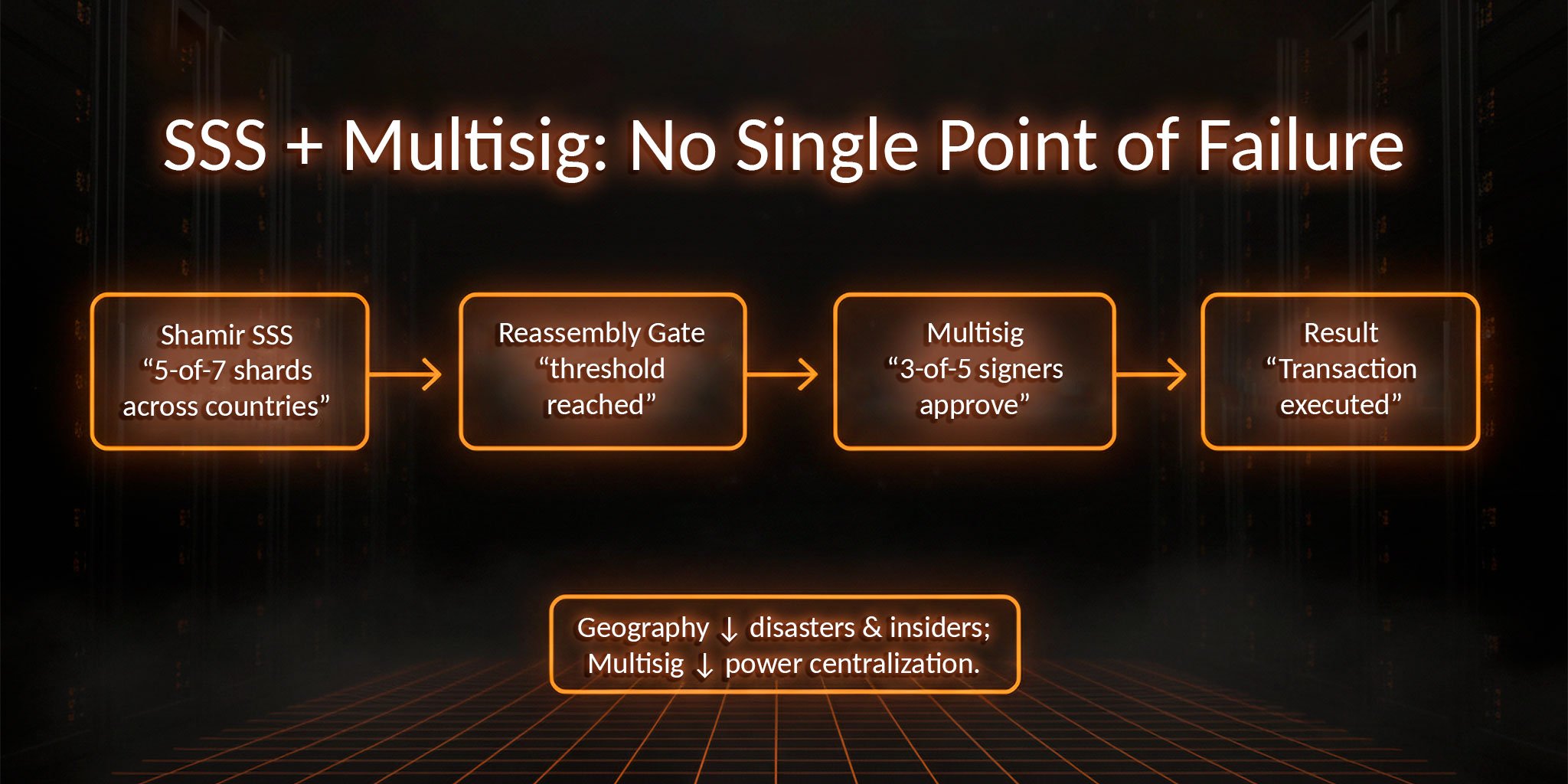
Together, they create a multi-factor architecture with interdependent access verification: even if someone gathers all the Shamir shards, the transaction won't go through without the multi-sig. Conversely, even a full multi-sig consensus is useless if the key isn't reassembled via Shamir.
How It Works in Practice
In 2025, many custodial platforms, banks, and institutional funds have integrated geo-distribution not only for storage but also for auditing, disaster recovery, and regulatory compliance. Geo-distribution is no longer an experiment—it's part of the operational model.
A corporation might split a master key using Shamir among seven locations in different countries, setting a "5-of-7" rule. But the assembled key doesn't work directly—it’s gated by a 3-of-5 multi-signature from trusted top executives or regional centers.
Thus:
Even compromising one link doesn't bring down the system. That's why in 2025, this approach has been adopted by funds, custodians, and exchanges managing billions.
For companies aiming for 2025-level crypto security, implementation requires a clear strategy:
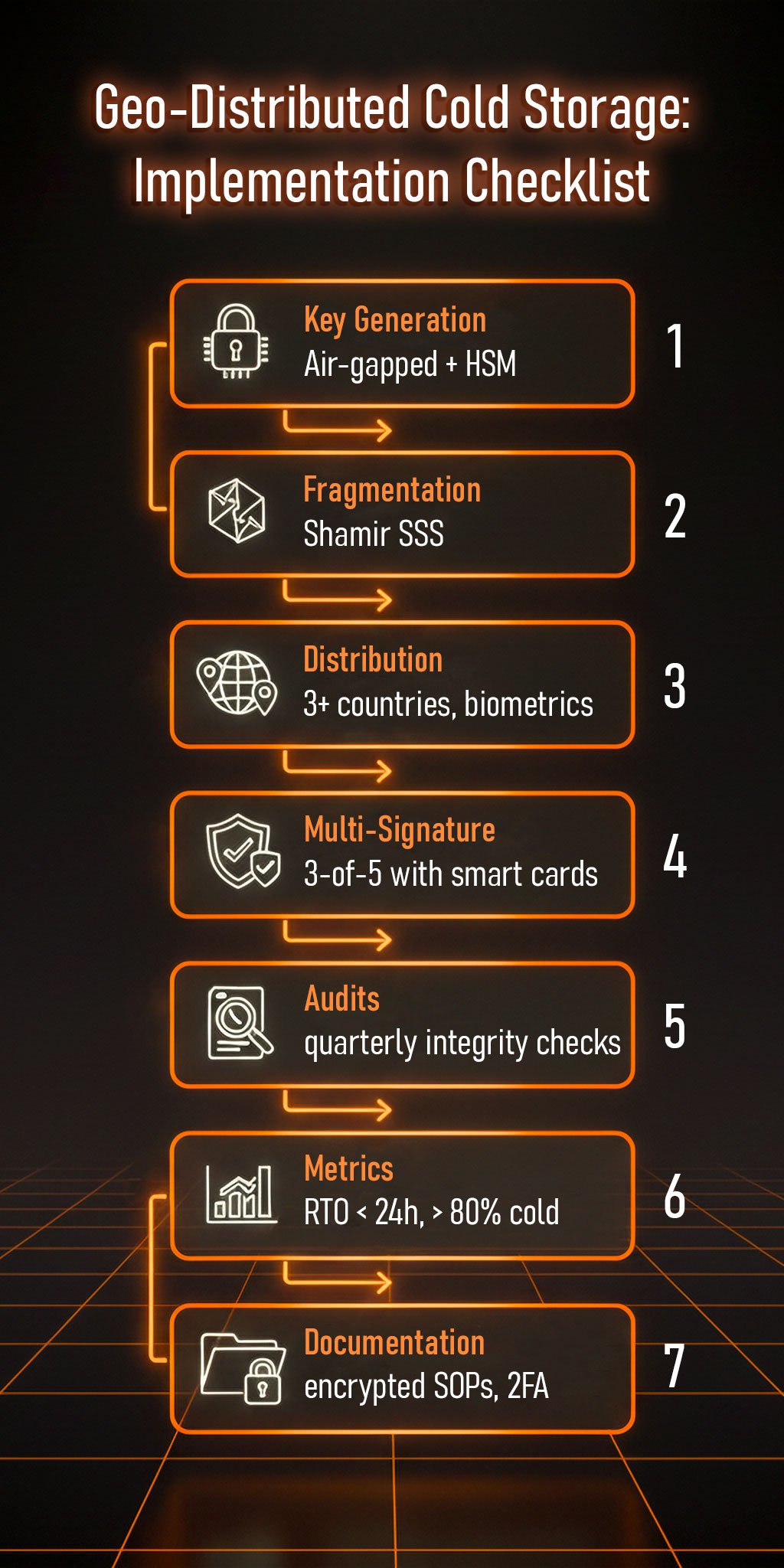
In 2025, Fireblocks saved $600 million by using this checklist: their keys, split with Shamir, were stored in 5 regions, and a multi-sig stopped an insider attack.
In a world where even the most reliable servers can suffer infrastructure failure from a single power outage or a regulator's visit, companies have stopped storing keys in one location.
Seed phrase shards and multi-signatures distributed across the globe have become a sign of strategic planning and high-level reliability. Exchanges and custodians operate on the principle that the architecture must be resilient to failures in key data centers or jurisdictions.
Effectively, geo-distribution has become a corporate standard for resilience. This approach enhances infrastructure robustness and makes it immune to the impact of events, authorities, or accidents. Without this approach, infrastructure is vulnerable to critical failures.